Is your dating app data safe?
You join a dating app, enter all your personal details and start your journey to find a great match. But:
- What happens to all of your data?
- Is it safe?
- Will it be erased when you leave?
No, can often be the answer if you’re not careful. Never mind the scammers on the sites, it’s the owners of the sites that could be the issue. There are dating brands (some of them very big) who do all sorts of things with your data that you may not be aware. This article is a way for you to test the sites you use and gives you an idea of how to better protect yourself. It has practical tips on finding how secure your dating app actually is and ways for you to try and hack your own data.
Terms and conditions
No one reads these, right? Only 0.19% of our website’s visitors read the terms and conditions. You really should as this is the best way to see if the site you’re about to join performs any unethical practices with your data. Most companies don’t break the law, they bend it by stating what they do in their terms and conditions in the hope you will not read them. Here are some of the types of things to look out for:
Reanimating dead profiles:
This is the process of taking an account that has not been used for a while and making it appear active, most often by sending messages on behalf of the inactive user. So you may have used a site, found a partner and left without deleting your account. You picture and profile is then becoming active again and communicating with other people!
Not deleting accounts:
There are many different things to look out for in the terms and conditions with deleting and removing data:
- Not deleting any data at all
- Not deleting partial / non complete sign ups
- No policy on removal of inactive accounts
Some dating brands keep hold on to as much data as possible to inflate their companies valuation. The more members they state adds value to the company and helps attract new users. If a company is stating millions of members you should consider if these are all active and/or completed profile registrations. Online dating is also a very male dominated industry. Deleting old male accounts and holding on to inactive female accounts is a way to make the male / female ratio close to 50 : 50.
Shared databases:
The are an estimated 40,000+ dating sites worldwide that are clones of other sites. These are know as white label sites. Individuals set them up with the help of a
provider to start their own dating site. A person who joins site A can have their data shown on site, B, C and D. Although your data is only stored in one
physical location you many not want to be associated with some other brands. For example, you could join a mainstream site and say that you like some fetish activities and then be shown on a number of hardcore bondage sites. Knowing all of the sites your data is shared on is near impossible as new sites
are being made every day.
Your location
Almost all dating apps today use the GPS system within the phone to set your location. This is easy for the user and also offers a degree of security as it takes a bit of effort to fake a location. However, there is a major privacy issue if the app you use stores your exact location. A compromised database would give away your location, if you set up your account at home then your home address would be easy to locate and may be used to subject you to blackmail when used with other data you provided such as sexuality or sexual preferences.With the help of some mathematics someone could find your home without ever hacking the database. Or if they are not good at maths they can do it with a map, compass (one for drawing circles) and a pen. This is now it’s done.
Step 1:
The baddie use app and checks in their location (A), and notes how many miles away you are. Most apps give the distance from one user to another.
Step 2:
The baddie then moves to another location (B), and updates their location and notes down how many miles you are away.
Step 3:
They do it one more time with a final location (C) and notes the distance.
As long as their 3 locations form a triangle, ideally with your location within the boundary of the triangle they can work out where you are. If you’re outside the boundary they just need to try more locations. The picture below shows an example of just how easy it is to reverse engineer someones location.
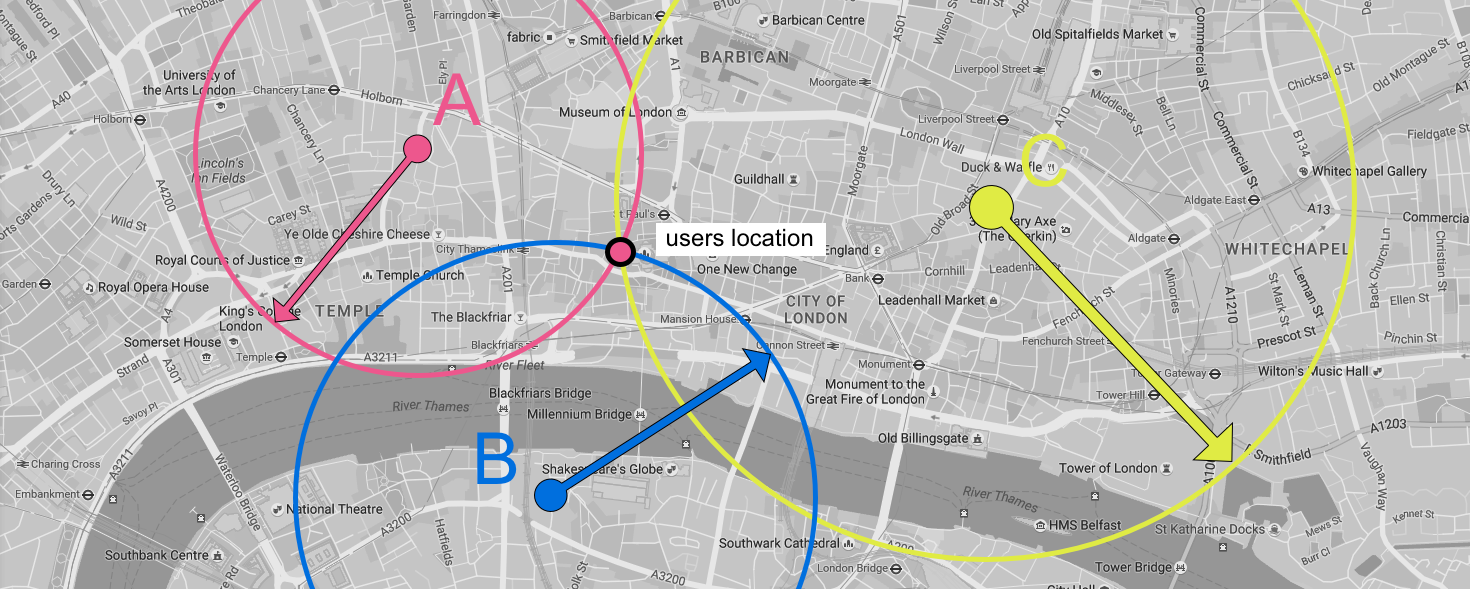
You need to be sure your dating app is storing an approximated location to stop your exact position being exposed. Your options if you don’t know their policy are to try and hack your own location via the method described above with the help of a friend who also uses the app or never checkin your location from your home address.
Passwords
The likely hood that your dating app has messed this up is quite high. There have been many dating site security breaches over the past years and other non dating sites, some of which are huge stock market listed brands and they have not secured their users passwords correctly.Almost every site you use needs a password and having different passwords for every site is just too complex so people tend to use the same password many times. The other issue is using passwords that other people use a lot. I will explain why this is an issue, keep focused as this can get a bit complex which is why so many companies take short cuts! But if you get to the end of it I will reward you with a way of finding out if your provider is not doing a good job.
Passwords should be hashed. This is very different to encrypted. I personally use the word encrypted on ooOo® as very few people know what hashing is.
A hash is a one way process that turns your password into a jumble of letters, numbers and symbols. There are many hashing functions with some wonderful names, one of the most common is called md5 and another is called Blowfish.
Quiz time:
Q: An md5 hash can be 1000 times faster to generate than a Blowfish hash. Which is best?
A: The slower, Blowfish hash is the best!
When a hacker gets hold of the database they will see a column of passwords. Worse case for you is your dating app has stored them in plain text. GAME OVER, the hacker has your password and your email address and can now test it on your Gmail, Hotmail, iCould accounts and then start to steal more data.
If the password is hashed with md5 it offers some protection but only if you chose a good password. Here is table of md5 hashes for common passwords.
| Users password | The hash (md5) |
|---|---|
| password | 5F4DCC3B5AA765D61D8327DEB882CF99 |
| god | A4757D7419FF3B48E92E90596F0E7548 |
| startrek | 29F491121C63AF2A883378C50E1F8D9F |
| starwars | 5BADCAF789D3D1D09794D8F021F40F0E |
| qwerty | D8578EDF8458CE06FBC5BB76A58C5CA4 |
The hacker will have a table of common md5 passwords, this is known as a rainbow table. It’s easy to make as they need a plain text password database hacked from another site and can make the md5 version in minutes and compare the results. As md5 is FAST, this is why it’s a liability.
Blowfish hashing is slow so making a rainbow table is a longer process but more importantly you can salt your Blowfish! I know this is now sounding like a recipe but adding salt (another set of random data) makes 2 identical passwords have a different hash value. See the examples below for one common password:
| Users password | The hash (Blowfish) |
|---|---|
| qwerty | $2a$10$M8ewCeJLOPPRM.k8jiOfTu8CF3w1DjINg6qNoSPeLv8lgN4eucvX2 |
| qwerty | $2a$10$rnIeYDvZBRjyreIKDS6A0ew7vz.9gaMIO2b8uK6ZkCfHOUfPb0kkG |
| qwerty | $2a$10$xNXPjIO6jIzWUcNYIMcANuVsqB.Py4hz9vvSjtT0eMQfp/nQQ1Xkq |
| qwerty | $2a$10$dWK9kFLVV/yZLQ8tuk.VVeNk0JJ.1pqgvMq0cwn32YKK2.NpnDlHW |
| qwerty | $2a$10$l5wi51mPcyybXUrdvdRvgOJm7kXDQoobydHPz.F2jpvgBdol2Zu/y |
Salt combined with Blowfishes slow running time means the only option is now brute force. The hacker has to guess a password, apply the salt and compare the results. This could take half a second per guess and with a complex password will take thousands of years to reverse engineer.
However, if one of the sites you use doesn’t do this correctly then potentially all your accounts are at risk if you use the same passwords. If you read an apps terms and conditions and privacy policy and you see no mention of password hashing then avoid them! Their lack of security puts your entire identity at risk!
So how can you test your dating app? You need to request your password via their forgot password tool. If it gives you your current password they are storing your password in plain text. If it sends you a link to a reset tool then it’s likely the password is being hashed. However you cannot know what type of hashing they are using.
Summary and practical tips
Read the terms and conditions of your dating app. If you want to speed up the process search for these words: Entertainment, Inactive, Dormant, SharedAttempt to hack your own location via GPS with the help of friend
Sign up with a newly created email address, don’t login and then try and sign up with the same address a month later and see if they deleted the account automatically.
Test to see if an app exposes your membership by using the reset password tool. Try this with an address you know exists on the app and a made up one, compare the output.
Reset your password and see if you get your old password back.
Contact customer support and ask them for your password, they should not know what it is!
If your not happy with any of the results you find from testing your current dating apps then request your data to be removed and ask for confirmation in writing. Finally, if there are any parts of my article that worry you please consider sharing it with your friends. Data security is an important issue that needs more awareness.